Is your PC running slow?
Keeping PC free of clutter can help in performance and can also increase valuable disk space.
Here are a few simple Steps for maintaining the performance of PC.
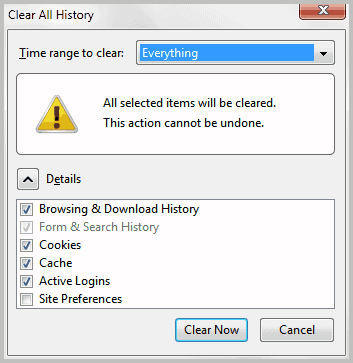
To clear cache in internet explorer
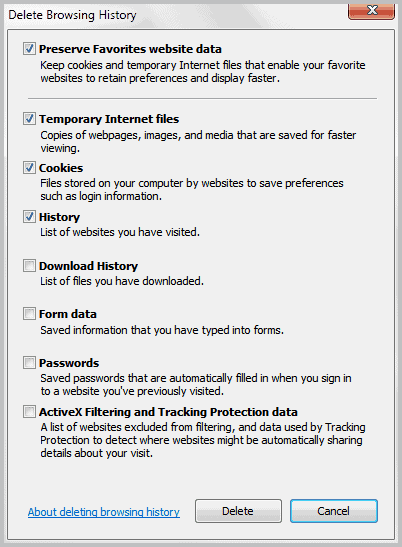
1. Click the Tools menu, and then click Internet Options.
2. Select the General tab, and then click Delete Files in the Temporary Internet files section.
3. In the Delete Files dialog box that appears, select Delete all offline content, and then click OK.
If it's the first time clearing the cache, or it's been a long while dumped the cache and the file accumulation is large, deleting these files might take several minutes. When the cache is cleared, click OK to close the Internet Options dialog box.
To remove the unwanted programs
1. Click Start, and then click Control Panel.
2. In this View, click Add or Remove Programs, then click Remove a program.
3. Scroll through the list and look at each program. Windows XP lists how often the program is used and what day it was last started.
4. Click the unwanted programs, and click Change/Remove, and then follow the prompts to uninstall it.
Then restart the computer after removing a program. After the computer is restarted, repeat this process to remove more programs.
In order to add or remove a Windows component:
1. Click Start, and then click Control Panel.
2. In this View, click Add or Remove Programs, then click Add a program.
3. On the left hand side of the menu, click Add/Remove Windows Components.
4. Follow the commands in the Windows Components Wizard.
Modify System Restore data
Windows XP provides the option to restore PC to a previous state by manually saving restore information. System Restore continuously monitors PC for changes, like file changes, application changes, or installations. System Restore takes a "snapshot" of PC at a given point of time and then stores each of these snapshots so that it can turn back any changes to a period before experiencing any problems.
These snapshots of whole system take up memory space. Delete older snapshots which are not required in order to clean up hard disk.
To delete System Restore snapshots except for the latest one:
1. Click Start, point to All Programs, point to Accessories, point to System Tools, and click Disk Cleanup.
2. Wait till the Disk Cleanup calculates free disk space.
3. Click the More Options tab, in the System Restore area, and then click Clean up.
Our expertss are available round the clock, 24x7 at your service; you can give us a call on our toll free number 1 855 883 3366 or you can visit our website @ http://www.leniotech.com
Keeping PC free of clutter can help in performance and can also increase valuable disk space.
Here are a few simple Steps for maintaining the performance of PC.
Run the Windows Live OneCare clean up scan
The clean up scanner itself checks hard disk for any unnecessary files and gives the option to delete them. Run the clean up scan in performing a disk cleanup—or run the complete full service scan to check for other PC issues as well.
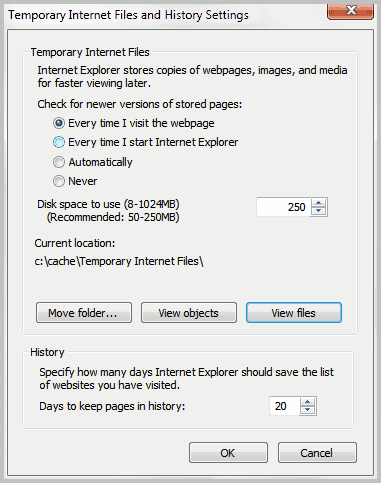
Clear Internet browser cache
The clean up scanner handles most frequent types of temporary files, but Internet browser automatically caches, or stores, another type of temporary file while surfing the Internet. Browsers like Internet Explorer save copies of the Web pages visited in order to load these pages faster while visiting those sites next time. Outside of speeding up browsing, still, browser does not require this cache of temporary files in order to operate properly. Since most of the Web sites have large graphics, clearing out browser's cache can save important hard disk space.To clear cache in internet explorer
1. Click the Tools menu, and then click Internet Options.
2. Select the General tab, and then click Delete Files in the Temporary Internet files section.
3. In the Delete Files dialog box that appears, select Delete all offline content, and then click OK.
If it's the first time clearing the cache, or it's been a long while dumped the cache and the file accumulation is large, deleting these files might take several minutes. When the cache is cleared, click OK to close the Internet Options dialog box.
Remove unused programs
Just because of using a program doesn't mean it isn't consuming resources and affecting PC's performance. Removing unused programs from hard disk is an easy way to maintain system and maximize available hard disk space.To remove the unwanted programs
1. Click Start, and then click Control Panel.
2. In this View, click Add or Remove Programs, then click Remove a program.
3. Scroll through the list and look at each program. Windows XP lists how often the program is used and what day it was last started.
4. Click the unwanted programs, and click Change/Remove, and then follow the prompts to uninstall it.
Then restart the computer after removing a program. After the computer is restarted, repeat this process to remove more programs.
Remove the optional Windows components
Remove optional Windows components from PC to free up space. Many components come normal with Windows, but may not use them frequently. Reinstall these components from Windows CD if it’s not needed later on.In order to add or remove a Windows component:
1. Click Start, and then click Control Panel.
2. In this View, click Add or Remove Programs, then click Add a program.
3. On the left hand side of the menu, click Add/Remove Windows Components.
4. Follow the commands in the Windows Components Wizard.
Modify System Restore data
Windows XP provides the option to restore PC to a previous state by manually saving restore information. System Restore continuously monitors PC for changes, like file changes, application changes, or installations. System Restore takes a "snapshot" of PC at a given point of time and then stores each of these snapshots so that it can turn back any changes to a period before experiencing any problems.
These snapshots of whole system take up memory space. Delete older snapshots which are not required in order to clean up hard disk.
To delete System Restore snapshots except for the latest one:
1. Click Start, point to All Programs, point to Accessories, point to System Tools, and click Disk Cleanup.
2. Wait till the Disk Cleanup calculates free disk space.
3. Click the More Options tab, in the System Restore area, and then click Clean up.
Our expertss are available round the clock, 24x7 at your service; you can give us a call on our toll free number 1 855 883 3366 or you can visit our website @ http://www.leniotech.com